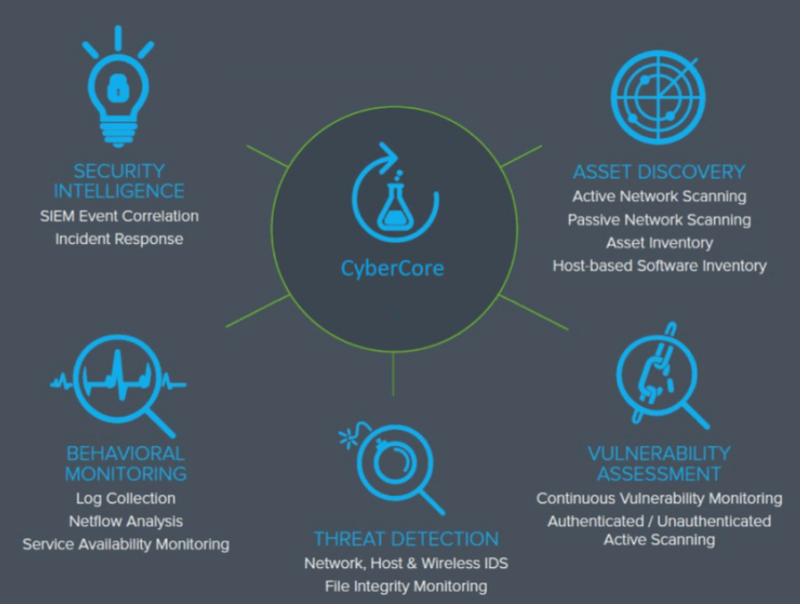
CYBER CORE

ARTIFICIAL INTELLIGENECE CYBER DEFENSE
Using proprietary machine learning and AI algorithms, the system passively analyzes raw network traffic to form an evolving understanding of ‘normal’ for every user, device, and subnet in an organization. Without presuming to know in advance what activity is ‘malicious’ or not, independently learns to detect significant deviations and immediately alerts the organization to emerging threats, from subtle insiders and low-and-slow attacks, through to automated viruses like ransomware.
Learn More
MOBILE DEVICE PROTECTION
Real-time intelligence feeds to security gateways protect against unknown malware, zero-day exploits and advanced persistent threats (APTs). Zero-day protection and advanced threat prevention against sophisticated 5th generation of cyber-attacks using patented multi-layered cyber security. End-to-end multi- layered cyber security protection for networks, endpoints, mobile devices, and cloud-based services.
Learn More
CELLPHONES AND TRANSMISSION DEVICES DETECTION
Accurate Detection - Future Proof - Multiple Alert Options. Deploy as a portable or network device with adjustable range.Zone Protectora and Zone Manager deliver real time protection with actionable intelligence. Active Monitoring Technology enables our customers to secure and protect their facilities, assets, and information worldwide.Zone Protector alerts and notifies as soon as a signal is detected. Secure classified information throughout your facility
Learn More
DOCUMENT RIGHTS MANAGEMENT
RightsManager enables best document security practices by allowing you to encrypt documents locally, so there is no need to upload unencrypted documents to an unknown server or file sharing site. You maintain complete control of your source files at all times.Once your files are encrypted, go ahead and share files securely through all the normal channels—email, website, intranet, cloud storage sites or removeable media. Recipients authenticate through a client/server interaction, denying access to any unauthorized recipients. With granular permissions policies for access, editing, printing and sharing, you can ensure recipients can only see what they need to.
Learn More
SECURE SIGN IN
Protects against phishing, man-in-the-middle and replay attacks with strong authentication Incorporates FIDO-certified security protocols, including public key cryptography/ infrastructure (PKI) Ensures security key and biometric information never leave the mobile device; no server-side secrets or link-ability between services or accounts.Facilitates higher user adoption: no need to remember passwords, no manual typing Works with smartphones that consumers/employees use every day. Delivers a consistent user authentication experience to access various services
Learn More